السَّلاَمُ عَلَيْكُمْ
Mohammed Afnaan Ahmed
Cybersecurity Researcher & Ethical Hacker
Securing the digital world, one vulnerability at a time.
About me:

I am a cybersecurity professional with a strong focus on web security, penetration testing, and offensive security, with a focus on understanding how real-world attacks work and how to defent against them effectively.
I hold the Certified Ethical Hacker Master (v13), CompTIA Security+ (SY0-701) and ISC2 Certified in Cybersecurity (CC) certifications, which validate my ability to secure systems, identify vulnerabilities, and respond to threats across modern IT environments.
My training has included structured coursework and hands-on labs, where:
- I actively spend time simulating real-world attack scenarios in controlled environments.
- I perform Vulnerability assessment and ethical hacking techniques.
- I perform Threat analysis and mitigation strategies to improve security baseline.
- I try to recreate real attack chains in controlled, isolated environments, and learn the TTPs of attackers
I am particularly drawn towards real-world attack vectors and spend time recreating them in controlled, isolated environments to sharpen my skills and understand the TTPs of threat actors.
Notable Research:
CVE-2025-14598
CVSS Score: 9.8 (Critical)
Discovered, reported, and supported remediation of a security vulnerability assigned CVE-2025-14598 through coordinated disclosure with CERT/CC.
Top Skills:
Security Testing
Linux
Windows
VMWare
Raspberry Pi
Networking
Python
Metasploit
Wireshark
MySQL
GitHub
C
Projects:

Raspberry Pi Pico HID Attack
The Raspberry Pi Pico acts like a keyboard and delivers malicious payload when this programmed with this script.
This script is powered by MicroPython and Adafruit library.
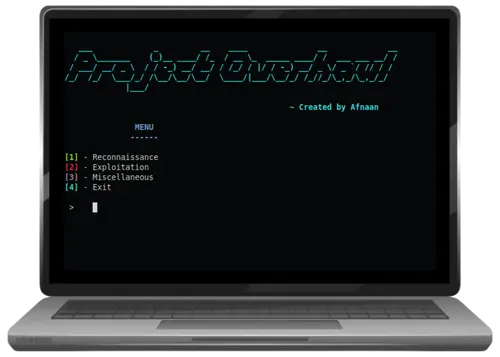
Project Overhaul
Project Overhaul integrates a variety of popular penetration testing tools into a single Command Line Interface.
The following tools are supported as of now:
Nmap, Netcat, Gobuster, Amass, Metasploit, Sqlmap, Hashcat, John the Ripper.
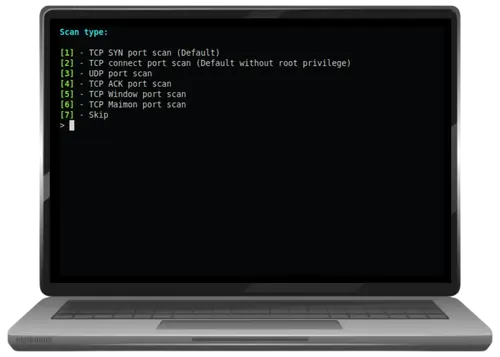
Nmap Command Generator
Interactive command-line interface (CLI) for inputting Nmap command and switches.
This script automatically generates Nmap commands based on user input.
Work & Study:
Internships
Freelancer
Cyber Security Consultant
09/2025 - 03/2026
The Red Users
Cyber Security Intern
11/2024 - 12/2024
Internshala Trainings
Ethical Hacking Trainee
05/2022 - 06/2022
Devskillhub training and consultancy
Frontend Development Intern
01/2024 - 03/2024
Cognifyz Technologies
Web Development Intern
12/2023 - 01/2024
Education
Bachelor of Technology
Computer Science and Engineering
Jawaharlal Nehru Technological University
2021 - 2025
Higher Secondary Education
Mathematics, Physics and Chemistry
Meluha Junior College
2019 - 2021
High School Education
General Studies
Kiddie Koop High School
2017 - 2019
What i'm looking for:
I am actively seeking cybersecurity roles globally, with a focus on penetration testing, network security, and ethical hacking. If you have an opportunity, let’s connect!







